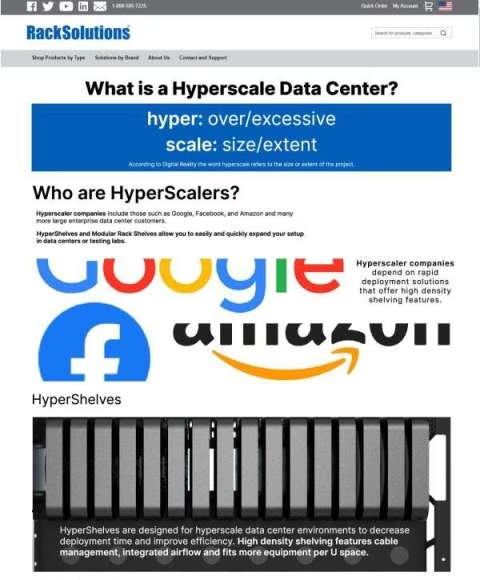
What is a Hyperscale Data Center?
Scaling IT environments efficiently is critical for success. RackSolutions’ Hyperscale solutions provide innovative shelving tools designed for high-density setups, airflow optimization, and streamlined cable management. Download this document to learn how RackSolutions supports hyperscale efficiency. Message to get started.