If your organization is planning to rely heavily on AI solutions over the next few years, wouldn’t it make sense to have a fleet built specifically for AI apps? Watch this video introducing #Microsoft Copilot+ PCs, the machines powered by a unique neural processing unit capable of 40 trillion operations per second that handles all of your AI needs with ease.
Blog
Microsoft Copilot for Security In Action
Lenovo Workstations: Rewrite What’s Possible with the ThinkStation P620

Check out this video on what creators around the world are doing with their @Lenovo ThinkSystem P620 workstation! See how it is changing the way people get things done with impressive results. After watching it, contact us to learn more about this workstation powered by the AMD Ryzen™ Threadripper™ PRO and NVIDIA® graphics.
How Prioritizing Cybersecurity Can Give Your Company A Competitive Edge
Thinking of ways to drive competitive differentiation? Consider positioning your company as a security-first organization. Great analysis:
Taking safety to new heights by speeding things up at the edge
Discover how Addfor is leveraging AI to strengthen public health measures with #Lenovo and NVIDIA! 👩⚕️ This article shows how they’re taking safety to new heights by speeding things up at the edge. Interested in your own Lenovo solutions for AI? Contact Tech Hero.
Your people work everywhere. Does your print solution?

For many organizations with work teams on hybrid schedules, printing has been a mess with employees using at-home printers for projects that should only be in the office and others having to make unscheduled office visits to print. How has your company handled this confusion? Take a look at this solution brief outlining the benefits of @HP Managed Print Services, which digitizes workflows, contains costs and builds an extra layer of security in your organization.
HPE Superdome Flex 280 Server
Getting started with Artificial Intelligence (AI)

Getting started with AI and #Lenovo! 🤖🙌 Check out this eBook for insights on how to get started with AI. It also defines the differences between AI, machine learning, and deep learning, and shows the technology needed to get the most from AI. If you’d like to learn more or explore Lenovo solutions for AI, contact Tech Hero.
Lenovo ThinkStation P620 Datasheet

Looking for a powerful, fast computer for multi-threaded applications? @Lenovo US ThinkSystem P620 powered by AMD Ryzen™ Threadripper™ PRO processor with NVIDIA® graphics has the performance and speed that demanding applications require. Check out the datasheet to see full options and specs, and contact Tech Hero to get yours today.
Invite Engagement with Partner
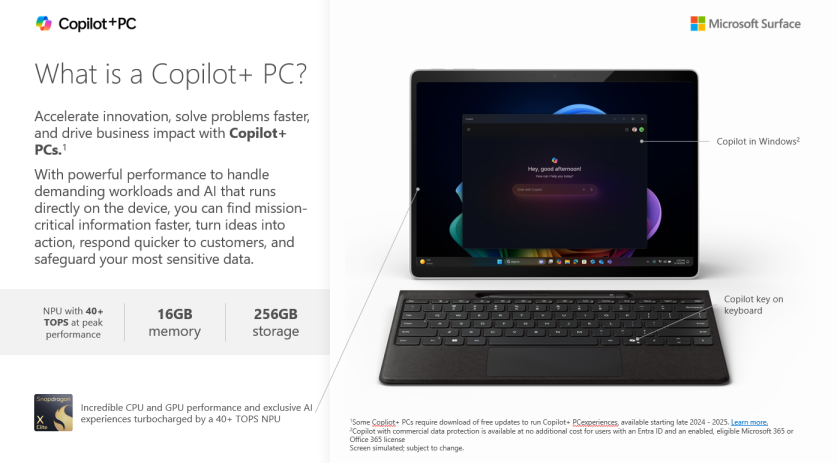
Imagine finding anything in your storage, no matter how siloed, in seconds. That’s possible with the powerful Windows 11 tool Recall, combined with a machine designed specifically for the AI experience like #Microsoft’s Copilot+PCs, powered by a neural processing unit capable of 40 trillion operations per second. See this technology in action: DM Tech Hero to get an eye-opening demo.



